Intro
Boost your cybersecurity with the Crown Jewel Defense Strategy. Learn 5 effective ways to protect your most valuable assets from cyber threats. Discover how to identify and prioritize crown jewels, implement robust access controls, and leverage threat modeling, incident response, and continuous monitoring to safeguard your organizations critical data and systems.
Implementing a Crown Jewel Defense strategy is a crucial aspect of protecting an organization's most valuable assets. A Crown Jewel Defense strategy is a comprehensive approach that focuses on identifying, protecting, and defending an organization's most critical assets, also known as "crown jewels." These assets may include sensitive data, intellectual property, or critical infrastructure. In this article, we will explore five ways to implement a Crown Jewel Defense strategy.
Understanding the Importance of Crown Jewel Defense

Before we dive into the implementation of a Crown Jewel Defense strategy, it is essential to understand its importance. A Crown Jewel Defense strategy is a proactive approach that helps organizations protect their most valuable assets from cyber threats, data breaches, and other types of attacks. By implementing a Crown Jewel Defense strategy, organizations can reduce the risk of data breaches, protect their reputation, and minimize financial losses.
Identifying Crown Jewels

The first step in implementing a Crown Jewel Defense strategy is to identify the organization's crown jewels. This involves conducting a thorough risk assessment to determine which assets are most critical to the organization's operations and reputation. The risk assessment should consider factors such as the asset's value, sensitivity, and potential impact on the organization if it were to be compromised.
Types of Crown Jewels
There are several types of crown jewels that organizations should consider when implementing a Crown Jewel Defense strategy. These include:
- Sensitive data, such as customer information or financial data
- Intellectual property, such as trade secrets or patents
- Critical infrastructure, such as data centers or network infrastructure
- High-value assets, such as valuable equipment or real estate
Implementing a Crown Jewel Defense Strategy
Once the organization's crown jewels have been identified, the next step is to implement a Crown Jewel Defense strategy. This involves developing a comprehensive defense plan that includes multiple layers of protection.
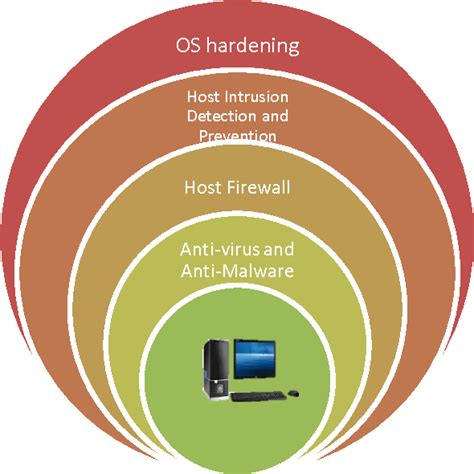
Layer 1: Network Security
The first layer of protection is network security. This involves implementing robust network security measures, such as firewalls, intrusion detection systems, and encryption. These measures help to prevent unauthorized access to the organization's network and protect against cyber threats.
Layer 2: Access Control
The second layer of protection is access control. This involves implementing strict access controls, such as multi-factor authentication, to ensure that only authorized personnel have access to the organization's crown jewels.
Layer 3: Data Protection
The third layer of protection is data protection. This involves implementing robust data protection measures, such as data encryption and backup systems, to ensure that the organization's crown jewels are protected against data breaches and other types of attacks.
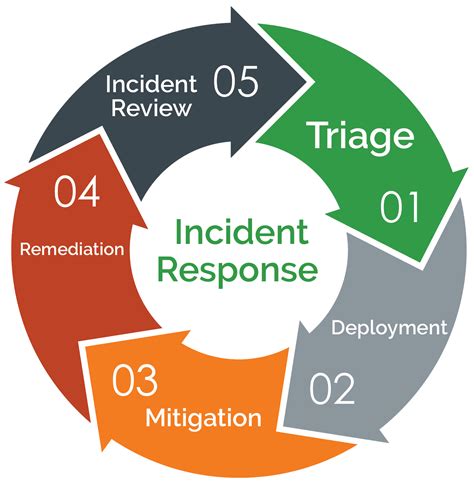
Layer 4: Incident Response
The fourth layer of protection is incident response. This involves developing an incident response plan that outlines the procedures for responding to a security incident, such as a data breach or cyber attack.
Layer 5: Continuous Monitoring
The fifth layer of protection is continuous monitoring. This involves continuously monitoring the organization's network and systems for potential security threats and vulnerabilities.
Benefits of a Crown Jewel Defense Strategy
Implementing a Crown Jewel Defense strategy provides several benefits to organizations. These include:
- Reduced risk of data breaches and cyber attacks
- Protection of sensitive data and intellectual property
- Minimized financial losses and reputational damage
- Improved incident response and recovery times
Conclusion
Implementing a Crown Jewel Defense strategy is a critical aspect of protecting an organization's most valuable assets. By identifying crown jewels, implementing multiple layers of protection, and continuously monitoring for potential security threats, organizations can reduce the risk of data breaches and cyber attacks, protect their reputation, and minimize financial losses.
Crown Jewel Defense Strategy Image Gallery






What is a Crown Jewel Defense strategy?
+A Crown Jewel Defense strategy is a comprehensive approach that focuses on identifying, protecting, and defending an organization's most critical assets, also known as "crown jewels."
What are the benefits of implementing a Crown Jewel Defense strategy?
+Implementing a Crown Jewel Defense strategy provides several benefits, including reduced risk of data breaches and cyber attacks, protection of sensitive data and intellectual property, and minimized financial losses and reputational damage.
How do I identify my organization's crown jewels?
+Identifying crown jewels involves conducting a thorough risk assessment to determine which assets are most critical to the organization's operations and reputation. The risk assessment should consider factors such as the asset's value, sensitivity, and potential impact on the organization if it were to be compromised.
