Intro
Unlock the mysteries of the First Hit Gray Zone concept. Learn how to master the art of stop-shooting decisions in self-defense, navigating the fine line between stopping a threat and excessive force. Understand the nuances of this critical zone and develop the skills to respond with confidence and precision in high-pressure situations.
The concept of First Hit Gray Zone has been gaining attention in recent years, particularly in the realms of cybersecurity and threat intelligence. However, many people still struggle to grasp the nuances of this complex idea. In this article, we will delve into the world of First Hit Gray Zone, exploring its definition, implications, and significance in today's digital landscape.
What is First Hit Gray Zone?
At its core, First Hit Gray Zone refers to the initial stage of a cyber attack or malicious activity where the attacker is attempting to gain a foothold within a targeted system or network. This zone represents a critical window of opportunity for defenders to detect and respond to the threat before it escalates into a full-blown breach.
During this phase, attackers often employ stealthy tactics to evade detection, using techniques such as social engineering, exploit kits, or zero-day vulnerabilities. The goal is to create a beachhead within the target environment, allowing them to establish a persistent presence and begin exfiltrating sensitive data or conducting further malicious activities.
The Gray Zone: A Delicate Balance
The term "Gray Zone" is used to describe the ambiguous nature of this initial stage, where the line between legitimate and malicious activity is blurred. In this zone, defenders must carefully balance the need to detect and respond to potential threats with the risk of false positives and unnecessary disruptions to legitimate business operations.
Key Characteristics of First Hit Gray Zone
To better understand the complexities of First Hit Gray Zone, let's examine some of its key characteristics:
- Stealthy Tactics: Attackers employ various techniques to evade detection, including encryption, code obfuscation, and anti-forensic tools.
- Initial Foothold: The primary goal of this stage is to establish a persistent presence within the target environment, often through the exploitation of vulnerabilities or the use of social engineering tactics.
- Evasion Techniques: Attackers may use evasion techniques, such as code manipulation or anti-debugging methods, to avoid detection by security controls.
- Network Exploration: Once inside, attackers may conduct reconnaissance to identify valuable assets, map network topology, and identify potential vulnerabilities.
Implications of First Hit Gray Zone
The First Hit Gray Zone has significant implications for organizations and individuals alike. Some of the key implications include:
- Increased Risk: The initial stages of a cyber attack can be particularly damaging, as attackers may be able to establish a foothold and begin exfiltrating sensitive data before detection.
- Evasion and Persistence: Attackers may employ various evasion techniques to maintain persistence within the target environment, making it challenging for defenders to detect and respond to the threat.
- False Positives: The Gray Zone can lead to false positives, where legitimate activity is misidentified as malicious, resulting in unnecessary disruptions to business operations.
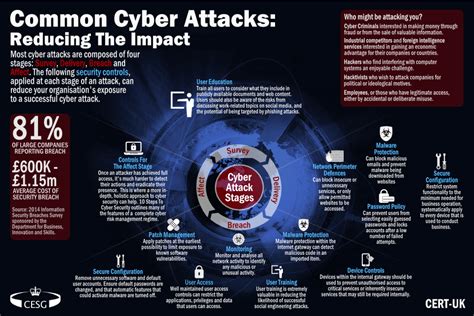
Detecting and Responding to First Hit Gray Zone
To effectively detect and respond to First Hit Gray Zone, organizations must employ a combination of security controls, threat intelligence, and analytics. Some strategies for detecting and responding to this stage include:
- Advanced Threat Detection: Implementing advanced threat detection solutions, such as machine learning-based systems, to identify suspicious activity.
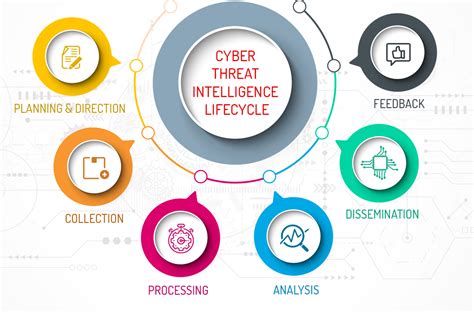
- Threat Intelligence: Leveraging threat intelligence to stay informed about emerging threats and tactics, techniques, and procedures (TTPs) used by attackers.
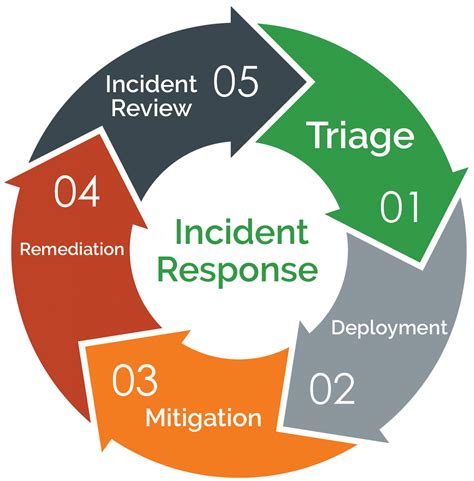
- Incident Response: Developing and implementing incident response plans to quickly respond to and contain potential threats.
Gallery of First Hit Gray Zone Images
First Hit Gray Zone Image Gallery





Frequently Asked Questions
What is the primary goal of the First Hit Gray Zone?
+The primary goal of the First Hit Gray Zone is to establish a persistent presence within the target environment, often through the exploitation of vulnerabilities or the use of social engineering tactics.
What are some common evasion techniques used by attackers in the First Hit Gray Zone?
+Attackers may use evasion techniques, such as code manipulation or anti-debugging methods, to avoid detection by security controls.
How can organizations detect and respond to the First Hit Gray Zone?
+Organizations can detect and respond to the First Hit Gray Zone by employing a combination of security controls, threat intelligence, and analytics, such as advanced threat detection solutions and incident response plans.
In conclusion, the First Hit Gray Zone represents a critical stage in the cyber attack lifecycle, where attackers attempt to establish a foothold within a targeted system or network. By understanding the characteristics, implications, and strategies for detecting and responding to this stage, organizations can improve their cybersecurity posture and reduce the risk of a successful breach.
