Intro
Discover the secretive world of military classified information. Learn the 5 ways governments keep sensitive intel under wraps, including encryption, compartmentalization, need-to-know access, surveillance, and advanced security protocols. Explore the strategies used to protect national security and keep confidential data safe from prying eyes.
The world of military classified information is shrouded in mystery, with various measures in place to protect sensitive details from falling into the wrong hands. From top-secret documents to clandestine operations, the methods used to keep classified info under wraps are as fascinating as they are crucial to national security.
Maintaining secrecy is a monumental task, especially in today's digital age, where information can spread like wildfire. Despite the challenges, military organizations around the world have developed sophisticated systems to safeguard classified information. Here are five ways military classified info is kept secret:
Encryption and Ciphers

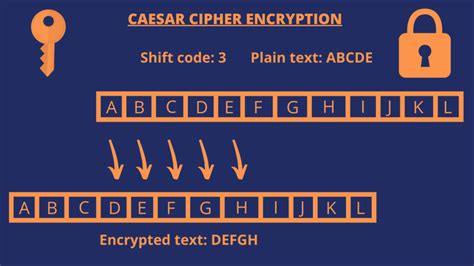
One of the primary methods used to protect classified information is encryption. By converting plaintext data into unreadable ciphertext, encryption ensures that even if sensitive information falls into the wrong hands, it will be unintelligible to unauthorized parties. Military organizations employ advanced encryption algorithms, such as AES-256, to secure their communications and data storage. Additionally, cryptanalysts use ciphers to further obfuscate encrypted data, making it even more difficult to decipher.
Need-to-Know Principle

The need-to-know principle is a fundamental concept in maintaining secrecy. It dictates that only personnel with a legitimate need to access classified information are granted clearance. This approach ensures that sensitive details are only shared among authorized individuals, minimizing the risk of unauthorized disclosure. By compartmentalizing access, military organizations can limit the spread of classified information and reduce the potential for security breaches.
Classified Document Control
Classified documents are strictly controlled to prevent unauthorized access. Military organizations use secure storage facilities, such as safes and vaults, to store sensitive documents. These facilities are designed to withstand physical breaches and are often equipped with advanced security systems, including alarms and motion detectors. Additionally, classified documents are typically marked with clear identifiers, such as classification levels (e.g., Top Secret, Secret, Confidential), to prevent misidentification and ensure proper handling.
Secure Communication Networks

Secure communication networks are essential for protecting classified information during transmission. Military organizations use specialized networks, such as the Joint Worldwide Intelligence Communications System (JWICS), to transmit sensitive information. These networks employ advanced encryption methods, secure authentication protocols, and intrusion detection systems to prevent unauthorized access. By using secure communication networks, military personnel can exchange classified information without compromising national security.
Intelligence Compartmentalization
Intelligence compartmentalization is a technique used to limit access to sensitive information within the intelligence community. By dividing intelligence into separate compartments, military organizations can control who has access to specific information and prevent unauthorized disclosure. This approach ensures that even if one compartment is compromised, the damage is contained, and other compartments remain secure.
Gallery of Military Classified Info
Military Classified Info Image Gallery






Frequently Asked Questions
What is the purpose of encryption in military communication?
+Encryption is used to protect sensitive information from unauthorized access by converting plaintext data into unreadable ciphertext.
What is the need-to-know principle in military secrecy?
+The need-to-know principle dictates that only personnel with a legitimate need to access classified information are granted clearance, minimizing the risk of unauthorized disclosure.
How do military organizations control access to classified documents?
+Classified documents are stored in secure facilities, marked with clear identifiers, and accessed only by authorized personnel with proper clearance.
In conclusion, maintaining secrecy in military operations is a complex task that requires sophisticated measures to protect classified information. By employing encryption, the need-to-know principle, classified document control, secure communication networks, and intelligence compartmentalization, military organizations can safeguard sensitive details and prevent unauthorized disclosure. As the world becomes increasingly interconnected, the importance of secrecy in military operations will only continue to grow.
