Intro
Strengthen your defenses with these 5 proven countermeasures to boost your security. Discover expert-approved strategies to prevent cyber threats, protect sensitive data, and safeguard your digital assets. Learn about threat intelligence, vulnerability management, incident response, access control, and encryption techniques to fortify your security posture and stay one step ahead of hackers.
The rise of technology has brought numerous benefits, but it has also introduced new risks. As we increasingly rely on digital systems, the importance of security has become paramount. Cyber threats, data breaches, and other forms of attacks can compromise our personal and professional lives. In this article, we will explore five proven countermeasures to boost your security and protect yourself from potential dangers.
In today's digital landscape, security is no longer a luxury, but a necessity. With the increasing number of cyber attacks, it's essential to take proactive measures to safeguard your digital assets. From individuals to organizations, security is a top priority. By implementing the right countermeasures, you can significantly reduce the risk of cyber threats and ensure a safe online experience.
Understanding the Threat Landscape
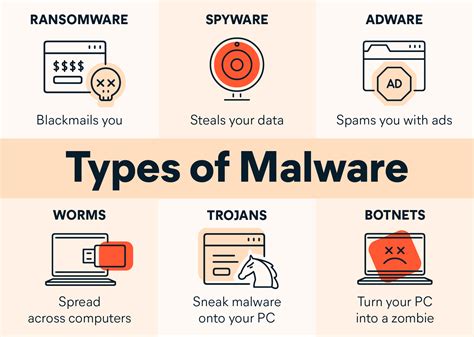
Before we dive into the countermeasures, it's essential to understand the threat landscape. Cyber threats are becoming more sophisticated, and attackers are using innovative methods to compromise systems. Some of the most common threats include:
- Phishing attacks
- Ransomware
- Malware
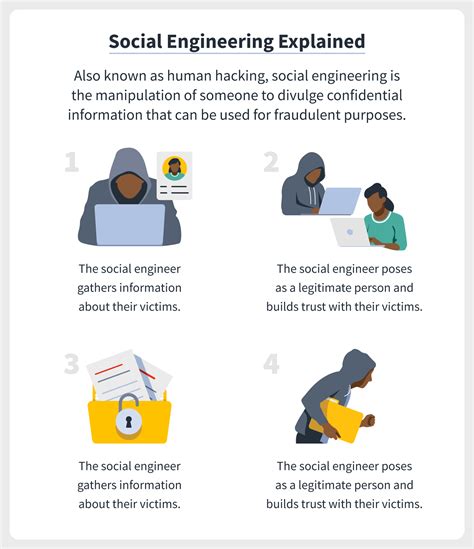
- Social engineering
- Denial of Service (DoS) attacks
These threats can have devastating consequences, including financial losses, reputational damage, and compromised sensitive information.
Countermeasure 1: Implement Strong Password Policies

One of the most effective ways to boost your security is to implement strong password policies. Passwords are the first line of defense against cyber threats, and weak passwords can be easily compromised. Here are some best practices to follow:
- Use a combination of uppercase and lowercase letters, numbers, and special characters
- Avoid using easily guessable information, such as names, birthdays, or common words
- Use a password manager to generate and store unique passwords
- Change passwords regularly, ideally every 60-90 days
- Enable two-factor authentication (2FA) whenever possible
Countermeasure 2: Keep Your Software Up-to-Date

Keeping your software up-to-date is crucial to patching vulnerabilities and fixing security flaws. Outdated software can leave you exposed to cyber threats, so it's essential to regularly update your operating system, browser, and other software. Here are some tips:
- Enable automatic updates for your operating system and software
- Regularly check for updates and install them promptly
- Use a patch management tool to streamline the update process
- Avoid using outdated software or plugins
Countermeasure 3: Use Encryption
Encryption is a powerful tool that can protect your sensitive information from unauthorized access. By encrypting your data, you can ensure that even if it falls into the wrong hands, it will be unreadable. Here are some ways to use encryption:
- Use a virtual private network (VPN) to encrypt your internet traffic
- Enable full-disk encryption for your device
- Use encrypted messaging apps, such as Signal or WhatsApp
- Encrypt sensitive files and documents
Countermeasure 4: Implement a Firewall

A firewall is a network security system that monitors and controls incoming and outgoing traffic. By implementing a firewall, you can block unauthorized access to your network and protect yourself from cyber threats. Here are some tips:
- Enable the firewall on your device and network
- Configure the firewall to block unnecessary ports and protocols
- Use a next-generation firewall (NGFW) for advanced threat protection
- Regularly update your firewall rules and configurations
Countermeasure 5: Use Anti-Malware Software
Anti-malware software is designed to detect, prevent, and remove malware from your device. By using anti-malware software, you can protect yourself from a wide range of cyber threats, including viruses, Trojans, and ransomware. Here are some tips:
- Install anti-malware software on your device
- Regularly update the software to ensure you have the latest protection
- Run regular scans to detect and remove malware
- Avoid using free or pirated anti-malware software
Gallery of Security Threats
Security Threats Image Gallery





Frequently Asked Questions
What is the most common type of cyber threat?
+Phishing attacks are one of the most common types of cyber threats. They involve tricking users into revealing sensitive information, such as passwords or financial information.
How can I protect myself from ransomware attacks?
+To protect yourself from ransomware attacks, make sure to regularly back up your data, use anti-malware software, and avoid clicking on suspicious links or attachments.
What is the best way to create a strong password?
+To create a strong password, use a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information, such as names or birthdays.
By implementing these five proven countermeasures, you can significantly boost your security and protect yourself from cyber threats. Remember to stay vigilant and continuously monitor your digital assets to ensure a safe online experience. Share your thoughts and experiences with us in the comments below!
